Kaspersky SIEM (Security Information and Event Management) – Next-Generation Protection
Kaspersky SIEM (Security Information and Event Management) – Next-Generation Protection
Couldn't load pickup availability
A State-of-the-Art SOC Platform: AI-Powered Technology Stack with Leading Threat Intelligence
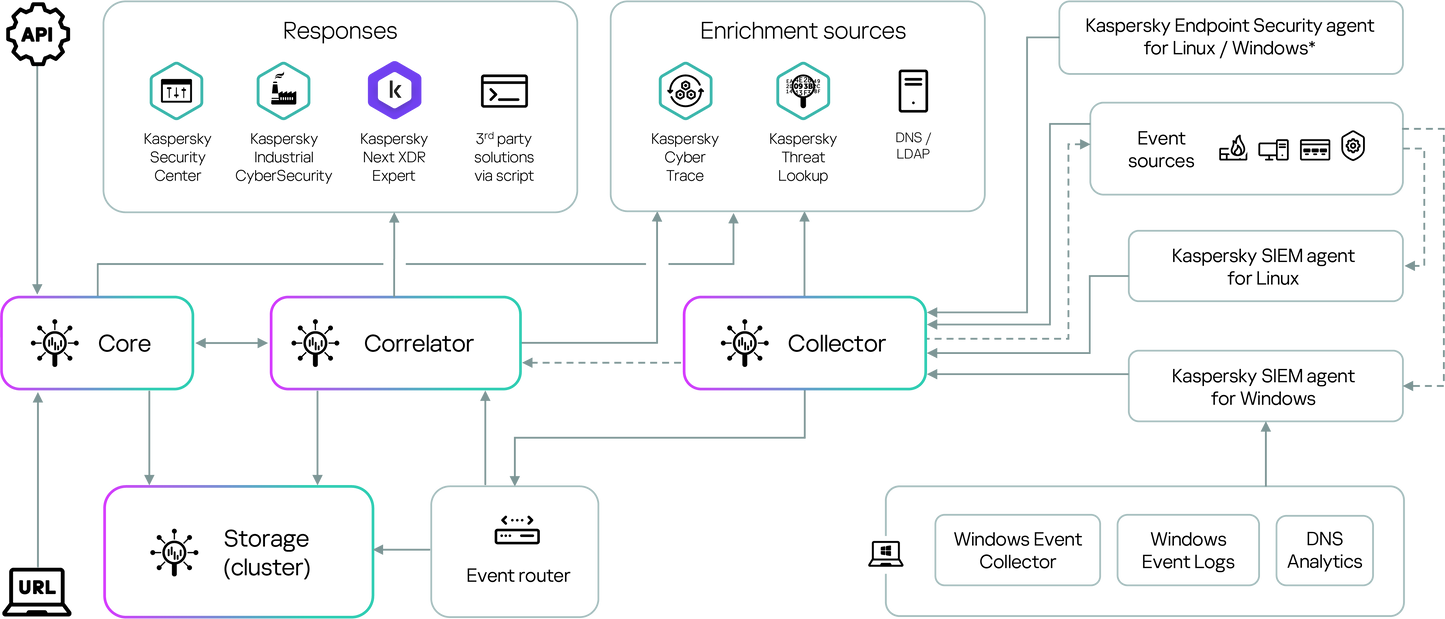
Kaspersky Unified Monitoring and Analysis Platform is an integrated next-generation SIEM solution for managing security data and events. By collecting logs from all security controls and correlating the data in real time, Kaspersky SIEM aggregates and provides all the information needed for incident investigation and response.
The platform not only collects, aggregates, analyzes and stores log data from the entire IT infrastructure but also provides contextual enrichment and actionable threat intelligence insights used by IT security experts for various use cases, including governance, compliance, and rule-based correlation matching for suspicious activity. The solution also supports the automation of responses to generated alerts and threat hunting.
Save up to 50% on system installation requirements
Save up to 50% on hardware or virtualization installation requirements and reduce TCO with a high-performance modular solution that consistently outperforms legacy SIEM vendors in terms of cost efficiency and can handle hundreds of thousands of EPS on each instance.
Stay flexible
Stay flexible with our licensing options. We track average flow of EPS per day after aggregation and filtering to limit overruns and do not restrict access to Kaspersky SIEM in case they happen.
Leverage built-in multitenancy
MSSP ready with native multitenancy support where a single SIEM installation in the main infrastructure of organizations enables the creation of isolated SIEM for tenants that receive and process their own events.
Store data in a low-cost, uncompromised fashion
Store data locally without going over budget for an extended period with hot and cold storage options, while still being able to search quickly across both areas simultaneously.
Benefit from a wide range of integrations
Benefit from a wide range of both Kaspersky and third-party integrations with built-in response options. Other vendors cannot match our level of seamless integration with our own products, which includes a single interface for Threat Intelligence integration, the capacity to use our endpoint sensors as SIEM agents, and much more.
Improve data relevancy, speed up detection and triage
Improve data relevancy, speed up detection and triage thanks to enrichment with tactical, operational and strategic Threat Intelligence provided via Kaspersky Threat Intelligence Portal by our world-leading team of researchers and analysts.
About the solution
Kaspersky SIEM integrates Kaspersky products and third-party solutions into a centralized information security system and is a key component in implementing a comprehensive defense approach capable of securing corporate and industrial environments, as well as detecting cyberattacks that start in IT and transition to OT systems.
Log management with data sovereignty
- Monitor, process, and store information about security events with a secure local storage of logs for regulatory compliance and incident investigation. Use historical data to quickly identify previously unknown threats with a powerful column-oriented database.
Real-time streaming correlation
- Real-time and historical correlation of security events with 650+ preconfigured correlation rules for detecting various attack scenarios regularly updated with MITRE mapping and response recommendations.
Tight integration with world-leading Threat Intelligence
- Improve data relevancy, speed up detection and triage thanks to enrichment with tactical, operational and strategic Threat Intelligence provided via Kaspersky Threat Intelligence Portal by our world-leading team of researchers and analysts.
24/7 Premium support and services
- Development of additional integrations by Kaspersky Professional Services representatives or partners, including the use of API capabilities of connectable products. Solution implementation on turn-key basis, support of migration to Kaspersky SIEM and more to ensure you get the most out of your installation.
Use cases
Kaspersky SIEM is designed to help organizations with established information security processes to increase their efficiency in the following tasks:
Centralized log management
- Collecting and storing events from a wide variety of sources in a central repository for future analysis.
Threat detection (security monitoring)
- Analyzing and correlating events in real time and receiving alerts about potential internal and external threats, while promptly detecting and prioritizing threats and reducing mean time to detect (MTTD).
Incident response
- Coordinating the response workflow, supporting analyst collaboration and reducing mean time to respond (MTTR), contain and remediate.
Threat hunting
- Fast discovery of previously uncovered threats with a powerful column-oriented database.
Compliance
- Complying with regulations, reporting incidents to national CERTs and gaining immediate visibility into security posture.
Our positioning
Decision-makers:
Chief Strategy Officer, VP of Security, CISO, CIO, SOC Manager.
Specifiers:
IT Manager, IT Security Manager, SOC Analyst, Incident Responder, Threat Hunter, CFO (Gatekeeper).
Segment:
MSSPs, mid-range and high-end enterprises, organizations in all industries with more than 1,000 endpoints and with internal IT-security expertise, organizations with regulatory and privacy concerns around data sharing and cloud usage.
Verticals:
- Financial services
- Healthcare
- Telecommunications & IT
- Retail
- Government and public sector
- Organizations with critical infrastructures.
Drivers:
Need for a unified solution to handle complex cyber-incidents, reduce detection and response gaps (MTTD, MTTR), improve Sec Ops efficiency and effectiveness, regulatory and policy compliance, analysis and reporting.
Pricing Model
Starting from: R24,999/year
Licensing model: Annual subscription based on average Events Per Second (EPS) after filtering and aggregation.
No penalties or access restrictions for EPS overages — usage is tracked and averaged to ensure flexibility and cost-efficiency.
MSP & Multitenant Pricing
Starting from: R3,000/month per tenant
Designed for MSSPs or IT providers managing multiple clients. Includes:
- Isolated tenant access
- Centralized administration
- Role-based access controls
- Optional bundled monitoring & response services
Volume-based discounts and custom packages available for 5+ tenants.
Optional Services
| Service | Once-Off Price (From) | Monthly (If Applicable) |
|---|---|---|
| Deployment & Setup (25–100 nodes) | R5,000 – R15,000 | — |
| Advanced Configuration (SIEM rules, MITRE tuning) | R4,500 – R10,000 | — |
| Monthly Monitoring & Reporting | — | R1,500 – R8,000 |
| Compliance & Report Automation | R5,000 – R20,000 | — |
| 24/7 Technical Support (Premium SLA) | — | R2,000 – R6,000 |
Watch: Kaspersky SIEM: Dashboards and Reports
Watch: Kaspersky SIEM: Distributed Deployment of SIEM
Watch: Kaspersky SIEM: Connecting SQL DB as a Data Source
Watch: Kaspersky SIEM: integration with Kaspersky Security Center and Assets Management
Watch: Kaspersky SIEM: working with Events (searching filters)
Share