Elite Cyberthreat Hunting Services: Unrivaled Cybersecurity Protection
Elite Cyberthreat Hunting Services: Unrivaled Cybersecurity Protection
Couldn't load pickup availability
Customized Threat Detection and Response Powered by Microsoft Defender XDR, Sentinel, and Global Threat Intelligence
At ThriftTech Solutions, our Elite Threat Hunting Service delivers advanced cybersecurity through expert-driven, custom threat hunting across endpoints, cloud, identities, networks, and workloads. Powered by Microsoft Defender XDR, Microsoft Sentinel, and enriched with global threat intelligence, we integrate comprehensive telemetry with tailored analytics to protect organizations worldwide from advanced persistent threats (APTs), insider risks, and zero-day exploits. Our service delivers measurable outcomes: reduced risk, accelerated response times, and compliance with global standards like POPI, GDPR, and HIPAA.
Value Delivered by Our Service
This Service provides concrete benefits through customized threat hunting and advanced technology, tailored for global organizations. Key outcomes include:
- Minimized Risk Exposure: Custom hunts, informed by global threat intelligence, detect and disrupt threats before they cause breaches or downtime.
- Rapid Incident Response: Automated attack disruption and 24/7 global SOC operations reduce mean time to respond (MTTR) to minutes.
- Global Compliance Readiness: Align with international regulations, including POPI (South Africa), GDPR (EU), HIPAA (US), CCPA (US), PCI-DSS, ISO 27001, APPI (Japan), and LGPD (Brazil).
- Operational Efficiency: Offload security management to our experts, enabling your team to focus on core objectives worldwide.
- Unified Global Visibility: Gain comprehensive insights across hybrid, multi-cloud, and on-premises environments with tailored analytics.
Comprehensive Technology Components
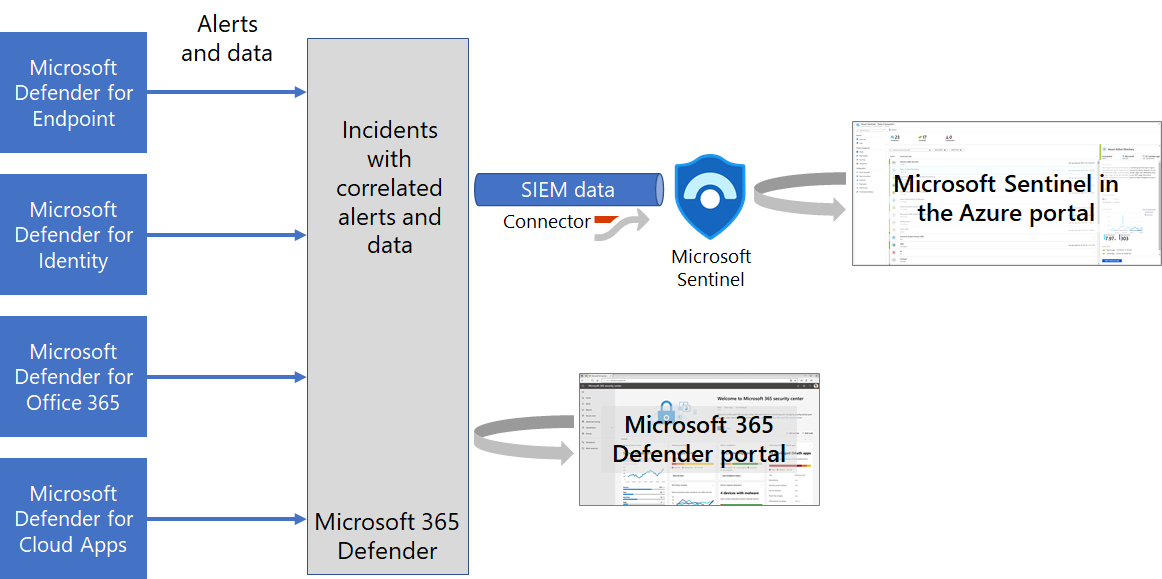
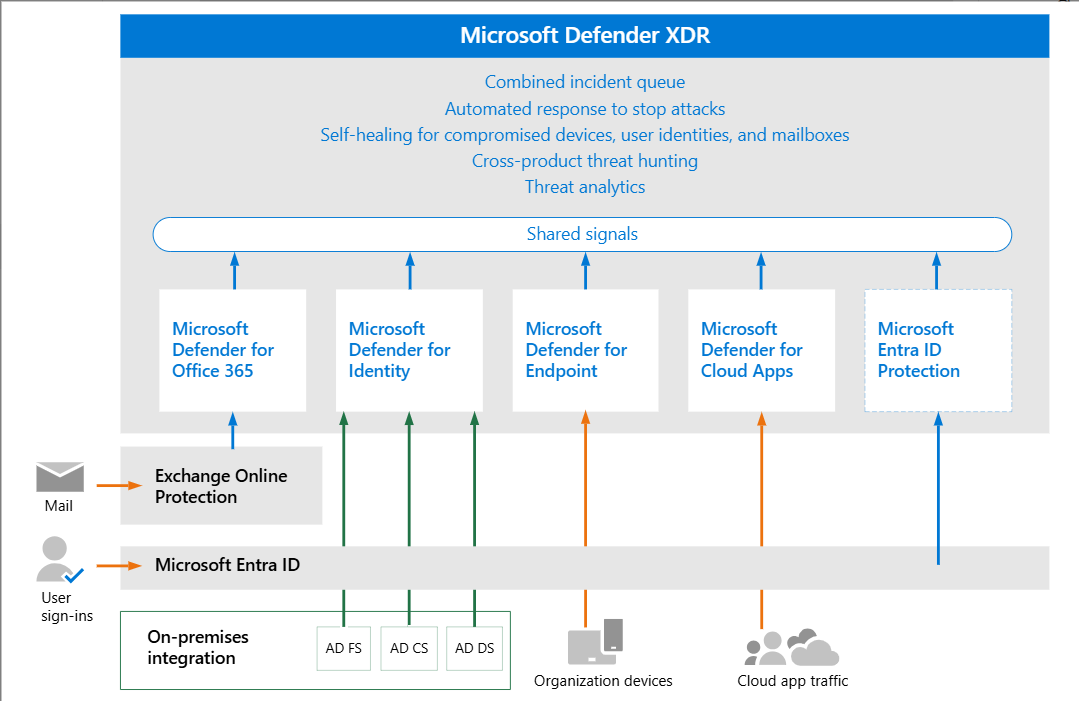
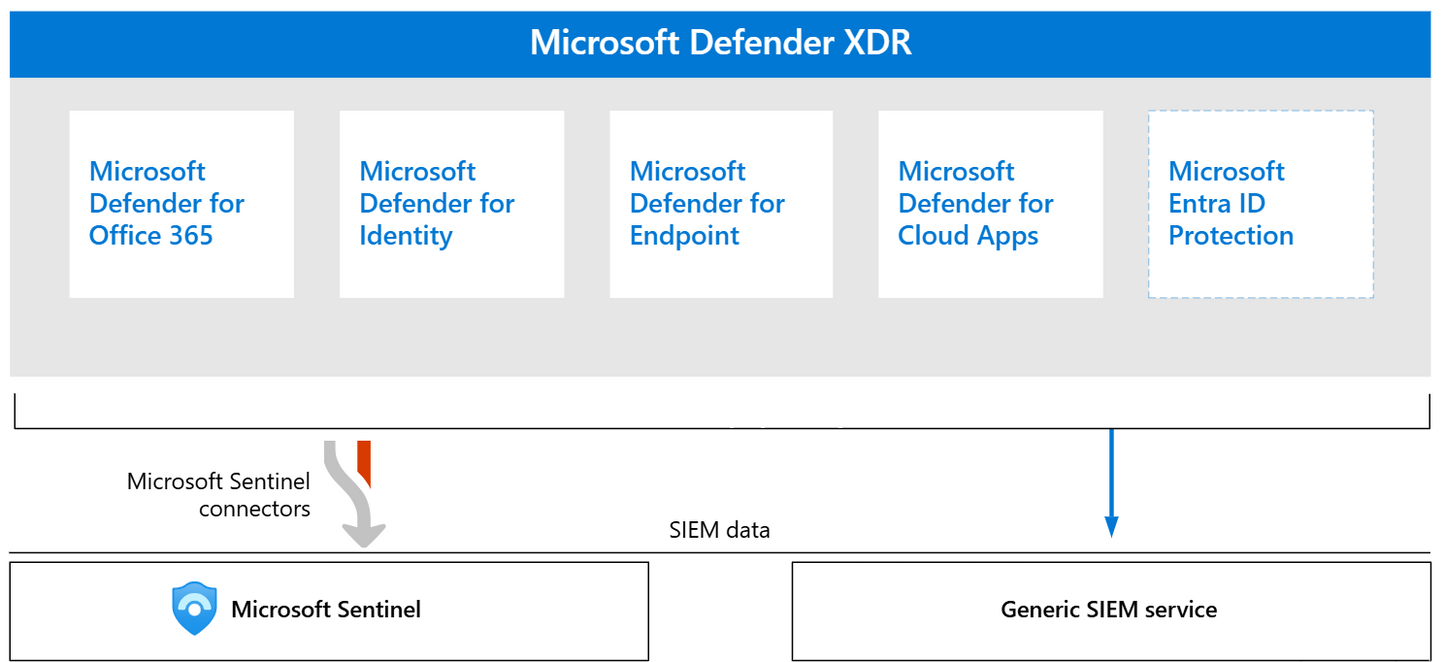
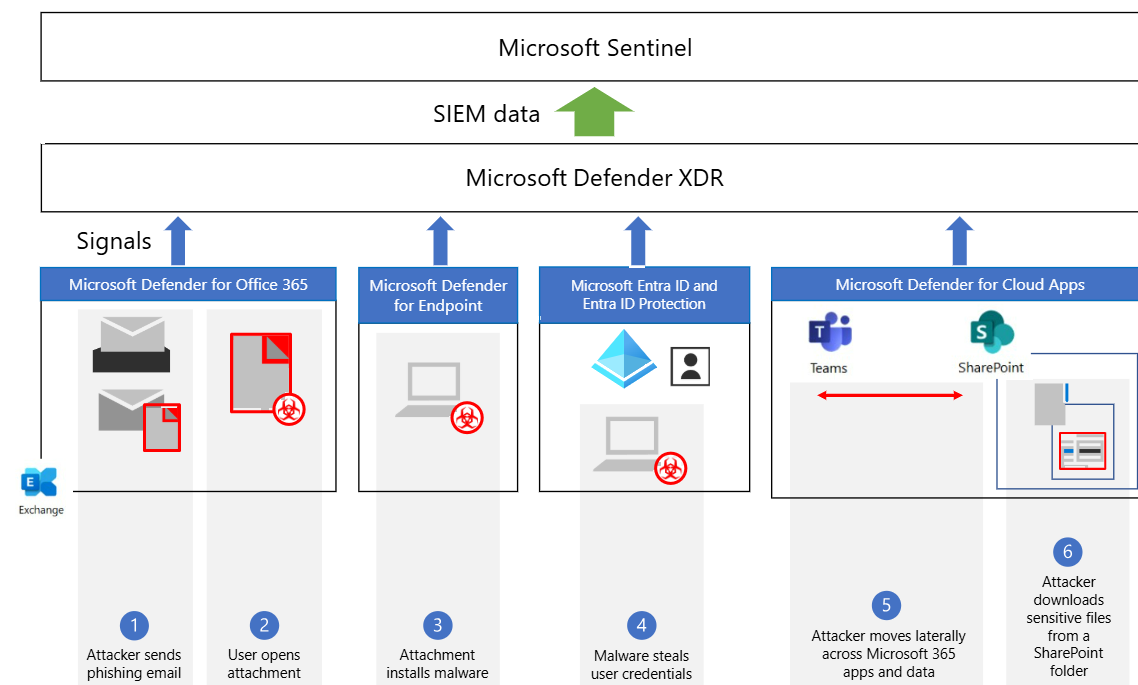
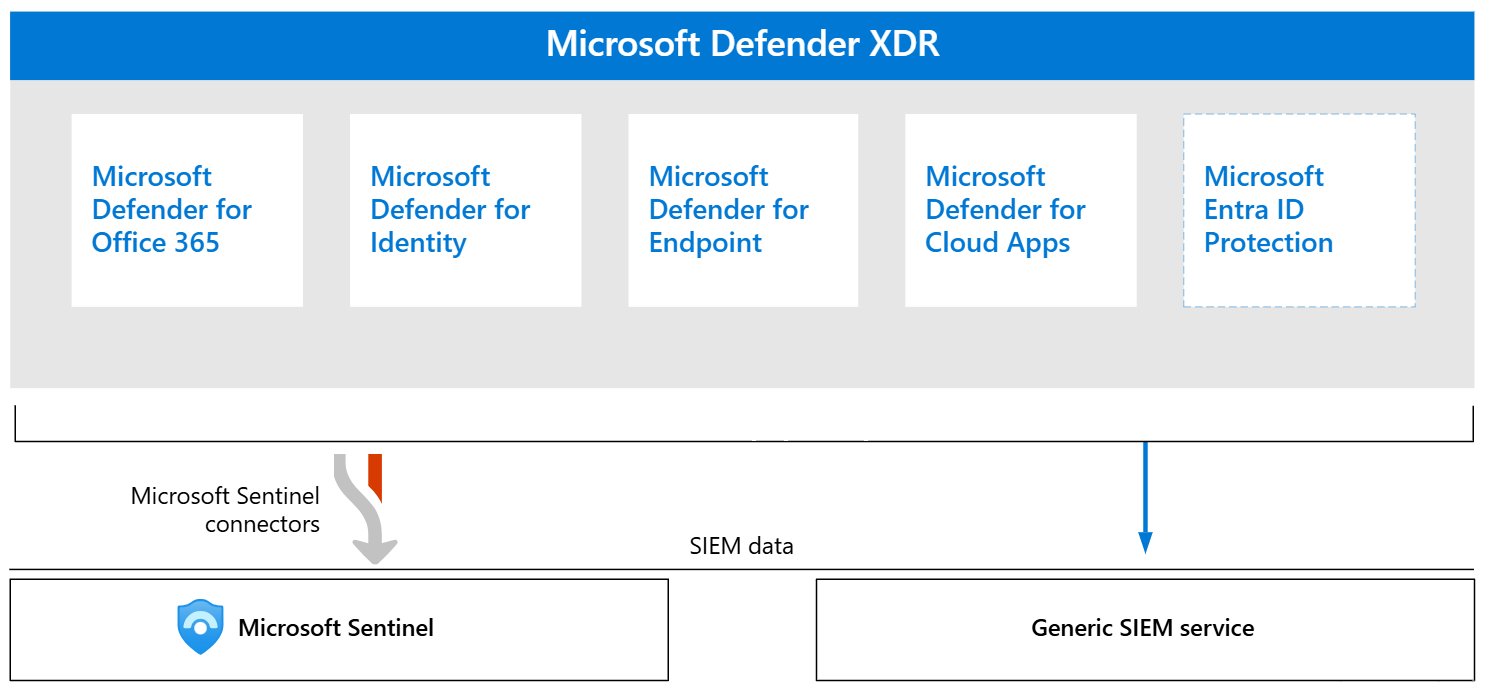
Our service leverages the full capabilities of Microsoft Defender XDR and Microsoft Sentinel, enhanced by global threat intelligence from MDTI and TAXII/STIX feeds. Below is how each component contributes to your protection:
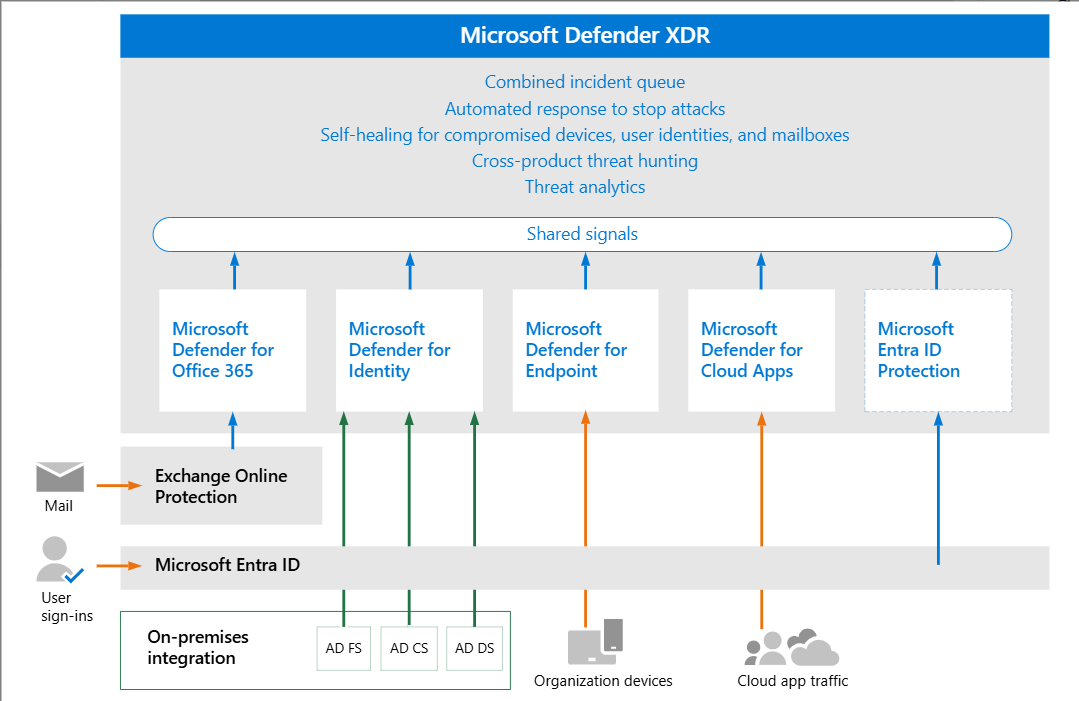
Microsoft Defender XDR
Defender XDR unifies multiple security layers for end-to-end threat detection, investigation, and response:
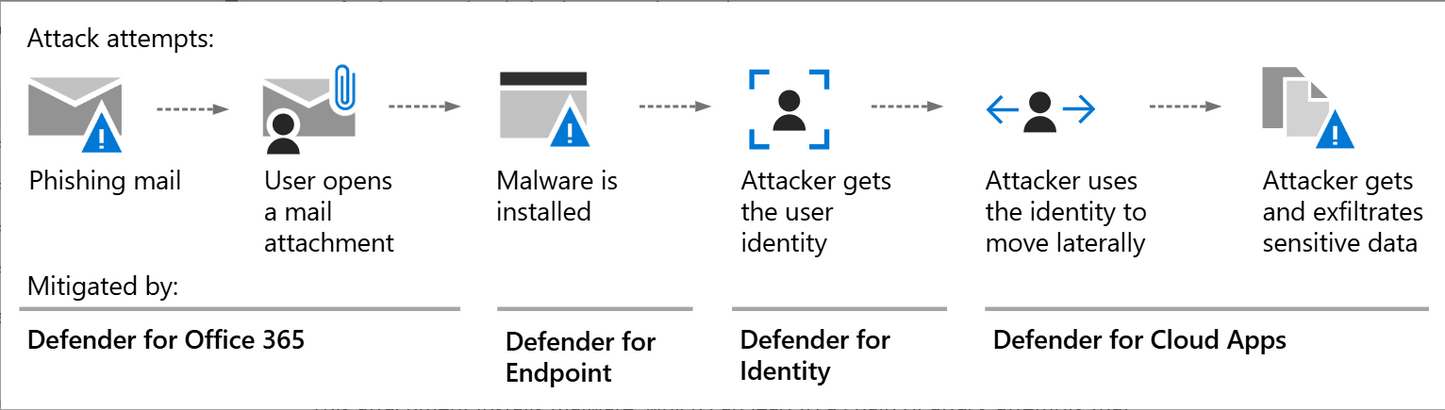
- Defender for Endpoint: Monitors devices for malware, ransomware, and suspicious processes using behavioral analytics, EDR, and automated attack disruption to stop threats like lateral movement or fileless attacks. Includes threat and vulnerability management (TVM).
- Defender for Identity: Detects identity-based attacks (e.g., pass-the-hash, Golden Ticket) by analyzing Active Directory signals and user behavior.
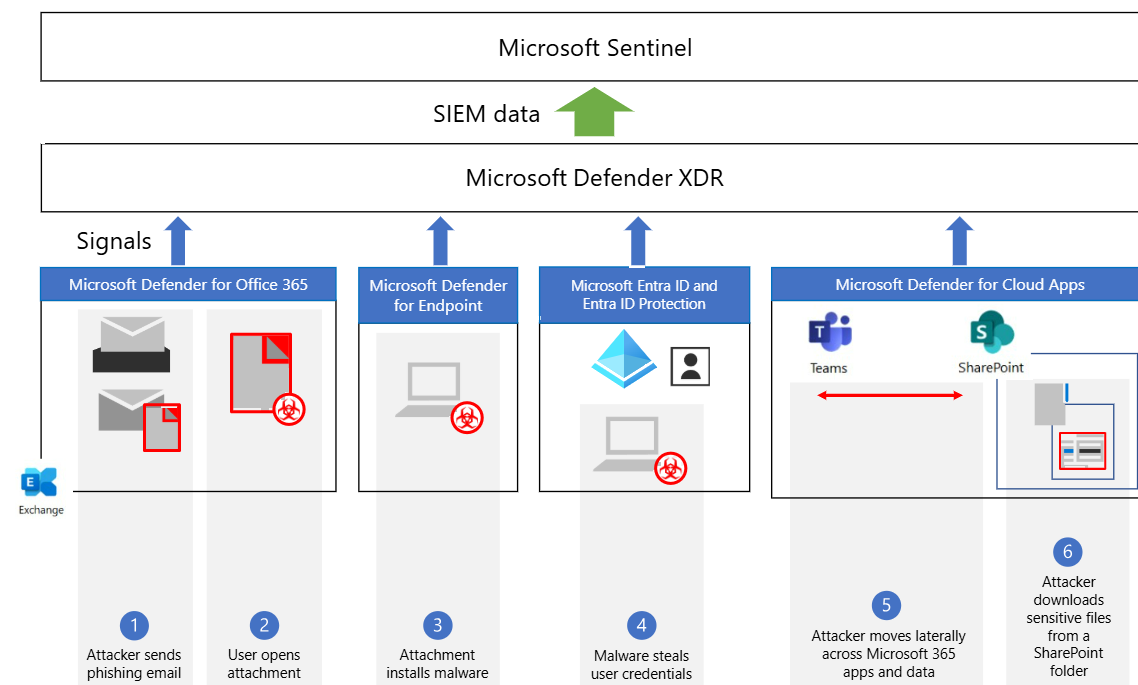
- Defender for Office 365: Protects email and collaboration tools from phishing and BEC using Safe Links, Safe Attachments, and anti-phishing policies. Supports post-breach investigation for Exchange, Teams, and SharePoint.
- Defender for Cloud Apps: Identifies shadow IT, insider threats, and misconfigurations in SaaS/IaaS applications, enforcing DLP and app governance.
- Defender for Cloud: Protects Entra (formerly Azure), AWS, Google Cloud, and hybrid workloads, detecting threats in virtual machines, containers, and databases.
- Attack Disruption: Automatically interrupts multistage attacks by correlating signals across domains, minimizing manual intervention.
- Advanced Hunting: Enables custom KQL queries across unified telemetry, hunting for anomalies like rare processes or suspicious connections.
- Incident Management: Consolidates alerts into prioritized incidents with cross-domain context.
- Threat Analytics: Provides reports on emerging threats, leveraging global threat intelligence.
- Microsoft Secure Score: Assesses and improves your security posture.
Microsoft Sentinel
Sentinel enhances our service with advanced analytics, automation, and scalability:
- Data Ingestion: Collects logs from Azure AD, AWS, Google Cloud, Microsoft 365, on-premises systems, and third-party sources, enriched with MDTI and TAXII/STIX feeds.
- Analytics Rules: Uses machine learning (e.g., Fusion) and custom KQL queries to detect threats like brute force attacks or data exfiltration.
- User and Entity Behavior Analytics (UEBA): Detects anomalous behavior (e.g., unusual logins) by profiling users and devices.
- Hunting Queries: Our analysts develop custom KQL queries, with Livestream for real-time monitoring of suspicious activities.
- Automation with Playbooks: Azure Logic Apps automate responses (e.g., isolating devices, blocking IPs).
- Workbooks: Deliver dashboards to visualize threat trends and compliance status.
- Cloud-Scale Retention: Supports retrospective hunting and compliance audits.
- Investigation Graph: Visualizes entity relationships to accelerate investigation.
- Content Hub: Integrates custom solutions for industry-specific detection.
- Anomaly Detection: Identifies novel threats using unsupervised machine learning.
Integrated Value
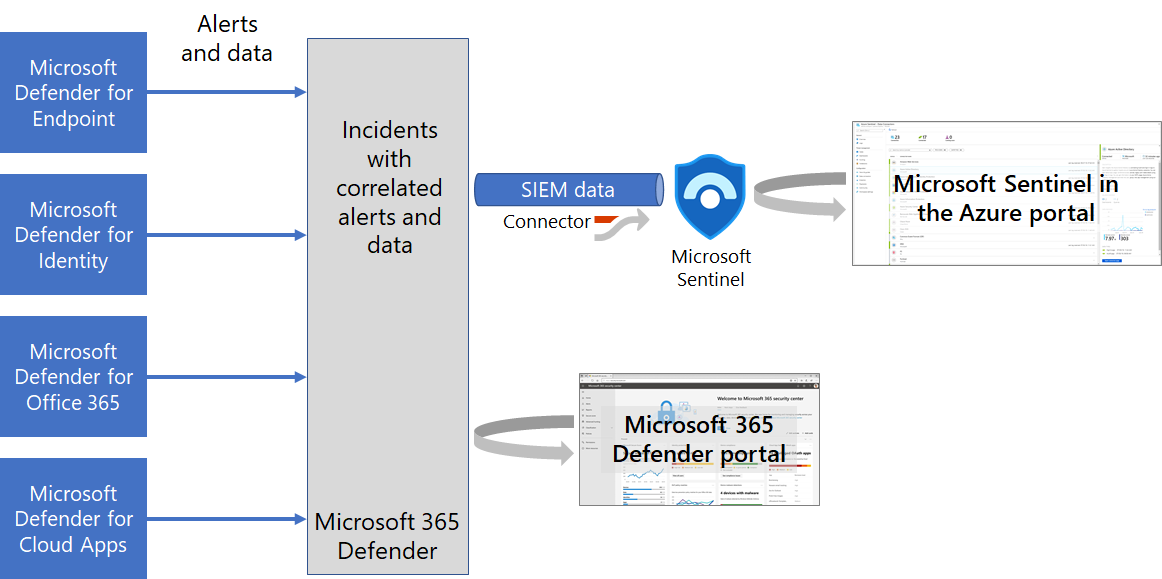
- Global Telemetry: Defender XDR streams data to Sentinel for cross-domain correlation.
- Custom KQL Queries: Tailored queries, enriched with global threat intelligence, ensure precision.
- Automated Attack Disruption: Defender XDR halts attacks early; Sentinel’s playbooks execute region-specific actions.
- Global Threat Intelligence: MDTI and TAXII/STIX feeds provide real-time TTP insights.
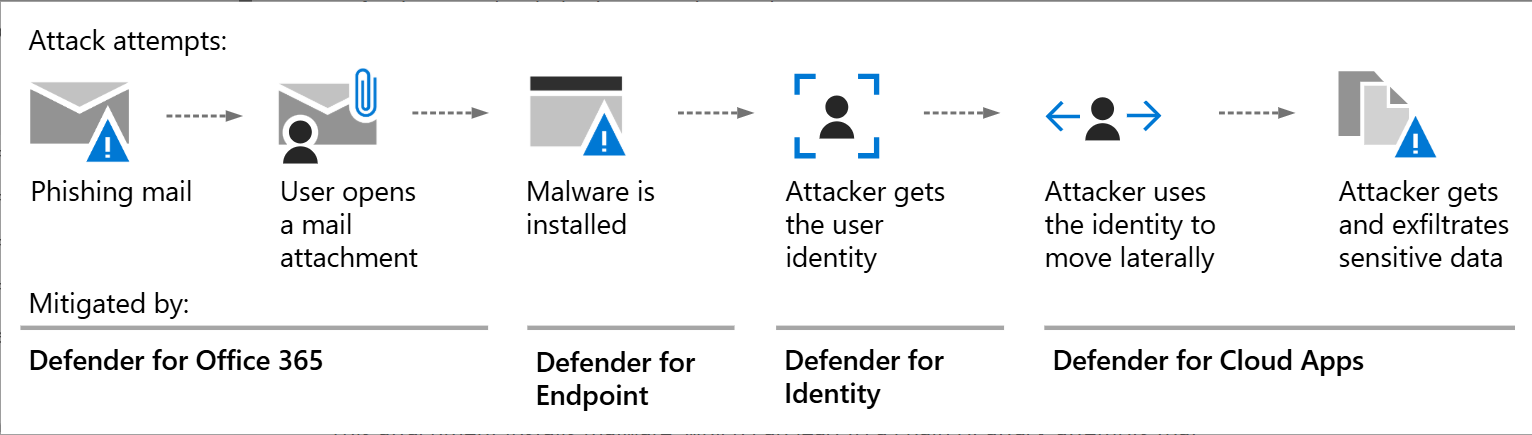
Our Threat Hunting Process
The service follows a tailored, expert-driven approach to deliver measurable security outcomes globally:
-
Global Environment Integration
We onboard your environment to Defender XDR and Sentinel, connecting data sources like Azure AD, Office 365, endpoints, cloud workloads, and third-party systems. -
Custom Hypothesis-Driven Hunting
Our analysts develop hypotheses based on MITRE ATT&CK, global threat intelligence, and your risk profile, designing custom KQL queries to search for anomalies (e.g., unusual file access, malicious IPs). -
Real-Time Global Detection
Sentinel’s Livestream and Defender XDR’s advanced hunting monitor for threats in real time, detecting activities like malware or privilege escalation. -
Validation and Response
Findings are validated against global threat intelligence. Automated playbooks execute immediate actions (e.g., device quarantine), while our 24/7 SOC handles complex investigations. -
Continuous Improvement
We refine KQL queries, update playbooks, and deliver reports to enhance detection and strengthen your security posture.
Sample KQL Query for Threat Hunting
Here’s a custom KQL query to detect suspicious network connections to known malicious IPs, leveraging global threat intelligence:
kql
DeviceNetworkEvents
| where RemoteIP in (ThreatIntelligenceIndicator | where IndicatorType == "IPAddress" | summarize by IndicatorValue | project IndicatorValue)
| summarize ConnectionCount = count() by DeviceName, RemoteIP, RemotePort, bin(TimeGenerated, 1h)
| project TimeGenerated, DeviceName, RemoteIP, RemotePort, ConnectionCount
Value: Identifies potential command-and-control activity, enabling rapid response to prevent data exfiltration.
Industries We Serve Globally
Our Threat Hunting Service is tailored to address the unique risks and compliance needs of every major industry worldwide:
- Financial Services: Secure transactions and detect fraud with real-time analytics.
- Healthcare: Protect patient data and ensure compliance with HIPAA, POPI, and GDPR.
- Retail & E-Commerce: Safeguard payment systems and customer data.
- Manufacturing: Defend production systems, IoT devices, and supply chains.
- Government & Public Sector: Meet global regulatory requirements.
- Business Process Outsourcing (BPO): Protect client data and call center operations.
- Mining: Secure operational technology and remote sites.
- Energy & Utilities: Defend critical infrastructure and smart grids.
- Technology & Software: Protect intellectual property and cloud systems.
- Education: Secure student data and e-learning platforms.
- Hospitality & Tourism: Protect booking systems and guest data.
- Transportation & Logistics: Safeguard supply chains and fleet systems.
- Telecommunications: Secure network infrastructure and customer data.
- Construction & Real Estate: Protect project data and smart buildings.
- Agriculture: Secure smart farming and supply chain data.
- Legal Services: Safeguard confidential client information.
- Media & Entertainment: Protect content distribution and streaming platforms.
Get Started Globally
Protect your organization, contact us to explore how we can address your cybersecurity needs.
- Consultation: Discuss your requirements with our experts at no cost.
- Demo: See our service in action, customized to your environment.
- Onboarding: Begin protection quickly with our region-agnostic setup.
Secure your global operations with a service engineered to stop threats early.
Frequently Asked Questions
What is threat hunting?
Our service proactively identifies hidden threats, such as malware or APTs, to prevent incidents worldwide.
How do Defender XDR, Sentinel, and global threat intelligence add value?
Defender XDR provides integrated telemetry and attack disruption, Sentinel enables custom analytics and data retention, and global threat intelligence ensures hunts are informed by the latest TTPs.
What is the response time for threats?
Automated playbooks and our 24/7 global SOC neutralize threats within minutes.
Can you support my industry and region?
Yes, we tailor our service for all sectors and regions, ensuring compliance with POPI, GDPR, and more.
Technical Details for IT Teams
- Defender XDR Components: Endpoint, Identity, Office 365, Cloud Apps, Cloud, with attack disruption, advanced hunting via KQL, threat analytics, Secure Score.
- Sentinel Features: Data ingestion, analytics rules, UEBA, custom hunting queries, playbooks, workbooks, cloud-scale retention, investigation graph, Content Hub, anomaly detection.
- Data Sources: Azure AD, AWS, Google Cloud, Microsoft 365, on-premises logs, MDTI, TAXII/STIX feeds.
- Automation: Azure Logic Apps for workflows like device isolation or IP blocking.
- Compliance: Supports POPI, GDPR, HIPAA, CCPA, PCI-DSS, ISO 27001, APPI, LGPD, and other standards.
- Integration: Seamless with Microsoft 365, Azure, AWS, Google Cloud, and third-party systems.
Request our Threat Hunting Service Whitepaper for a detailed overview or schedule a technical demo.
Flexible Threat Hunting Options: Per-Query, Per-Hunt, and Quick Consultations
For organizations seeking targeted, on-demand threat hunting, ThriftTech Solutions offers flexible, chargeable options: Per-Query Threat Hunting, Per-Hunt Investigations, and Quick Consultations. These services provide custom, expert-driven insights without long-term commitments, leveraging Microsoft Defender XDR, Sentinel, and global threat intelligence. Below are the offerings, pricing in South African Rand (ZAR) with US Dollar (USD) estimates, and scenarios illustrating their value:
Per-Query Threat Hunting
- Description: Our analysts craft and execute a single, custom KQL query to investigate a specific threat or anomaly in your environment, delivering a detailed report with findings and recommendations.
- Pricing: ZAR 999 (USD 53) per query (includes query design, execution, analysis, and report).
- Value: Pinpoint specific risks (e.g., suspicious login patterns) with rapid, actionable insights, ideal for one-off investigations.
- Scenario: A financial services firm in Johannesburg suspects a brute force attack on its Azure AD accounts after noticing login anomalies. ThriftTech designs a custom KQL query to analyze failed login patterns, identifies a targeted attack from a known malicious IP, and provides recommendations to block the IP and enforce MFA, preventing account compromise within hours.
Per-Hunt Investigations
- Description: A comprehensive threat hunt based on a tailored hypothesis, using multiple custom KQL queries across Defender XDR and Sentinel telemetry. Includes validation against global threat intelligence and a detailed report with remediation steps.
- Pricing: ZAR 4,999 (USD 275) per hunt (includes hypothesis development, multi-query execution, validation, and report).
- Value: Thoroughly investigates complex threats (e.g., potential APTs), reducing dwell time and preventing escalation.
- Scenario: A mining company in Australia detects unusual network traffic from a remote site. ThriftTech conducts a per-hunt investigation, developing a hypothesis around lateral movement, executing queries to uncover a fileless malware campaign, and validating it against MDTI. We provide a playbook to isolate affected devices, stopping the attack before data exfiltration.
Quick Consultations
- Description: A 60-120 minute session with a ThriftTech threat hunting expert to address urgent concerns, validate findings, or strategize responses. Includes a summary report with actionable advice.
- Pricing: ZAR 2,499 (USD 150) per consultation (includes expert analysis, discussion, and report).
- Value: Immediate access to expert insights for time-sensitive issues, enhancing decision-making and response.
- Scenario: A BPO provider in the Philippines faces a suspected phishing campaign targeting its call center staff. During a quick consultation, our expert analyzes email logs via Defender for Office 365, confirms a BEC attempt, and advises on deploying Safe Links and user training, mitigating the risk before sensitive client data is compromised.
Why Choose These Options?
- Customized Precision: Each query, hunt, or consultation is tailored to your environment and informed by global threat intelligence.
- Rapid Delivery: Results delivered within 24-48 hours, ensuring timely action.
- Scalable Expertise: Ideal for organizations needing ad-hoc support or complementing existing security teams.
- Global Compliance: Aligns with POPI, GDPR, and other standards, ensuring regulatory adherence.
Take the Next Step
Enhance your global security with the Elite Threat Hunting Service from ThriftTech Solutions. Request a consultation to learn how we can deliver measurable value.
Share